3 Comments
Working from home is the new reality for many people these days. As part of this new world, we are using our internet tools more and more, challenging the safety and security of these electronic systems likely to a degree not seen before. It is with that in mind that I would like to take a few minutes in this, and upcoming, posts reminding everybody about the importance of cybersafety in our online lives.
Imagine this scenario: Last night, unknown intruders vandalized the office suite next door. They shattered glass, busted locked doors open, rifled through drawers, and stole some computers. By the elevators, you see shards of shattered glass and “Do Not Cross” police tape.
Are you upset?
Scenario 2: Last night, unknown hackers broke into the computers of the office suite next door. They stole years of priceless, sensitive data. Nobody knows yet that anything happened, though a few employees are calling IT because certain apps aren’t working quite right. Otherwise, no one is talking. By outward appearances, nothing is amiss.
Are you upset?
Scenario 3: Last night, someone hacked into your computer. You don’t know that you’ve been hacked, but you do know that your computer is extraordinarily sluggish and that you are having trouble accessing your files. You call in your top IT person – someone known as “the genius” – and within a few hours, everything appears to be back to normal.
Do you say thank you? And if so, to whom?
Scenario 4: Last night, someone attempted to hack into your computer, but because you and your institution have created a culture that takes cyber safety seriously, the hacker couldn’t get in. Your computer is working just fine – all apps are functioning normally, and you are able to access the information you need to get your work done. You are completely unaware that an attempted attack was ever made.
Do you say thank you? And if so, to whom?
Here’s my guess about how most of us would answer the questions:
Scenario 1: Very upset! Frightened, scared.
Scenario 2: Not at all concerned, not even aware anything’s amiss.
Scenario 3: Yes, of course you would say, “Thank you.” You are impressed and grateful. You might even write a follow-up email or hand-write a thank-you card.
Scenario 4: Of course not – it’s just another day at the office.
These scenarios illustrate some of the key challenges around safety issues that you might not see in person, like those in the cyberworld. The reality is that most of us do not pay close attention to cyber safety until something is clearly wrong. Even then, we may not see the impact of a cyberattack as equivalent to that of a physical act of aggression or theft. Because we do not fully understand or acknowledge the danger of cyberattacks, we may not take appropriate precautions to prevent them, even though those risks can pose a formidable threat to our research and ability to achieve our mission. In today’s increasingly digital and connected world, it’s time to shift this attitude. We all need to acknowledge the risk inherent in cyber and take a personal stake in our shared responsibility for ensuring that NIH stays safe from cyberattacks.
I’d like to take this opportunity to thank my IT and privacy colleagues at NIH, who are constantly thinking about cyber safety and working tirelessly to keep us all safe. Recently, Dr. Francis Collins, the Director of NIH, sent a message to launch NIH’s Cyber Safety Awareness campaign, which emphasized how Cyber Safety is not solely the responsibility of staff in information technology, security, or privacy functions; it’s the concern of the whole NIH community. I support Dr. Collin’s effort to shift this accountability across all our staff, from interns to executive leadership. I am glad that all Leadership will address cyber safety as a top priority, since we simply cannot afford devastating setbacks to our research and mission.
I’d also like to thank former Assistant Attorney General John Carlin, whose book Dawn of the Code War deeply impressed (and frightened) me. In his book, Carlin reflects on the parable of Rome’s downfall as a metaphor to remind us about the need to be ever-vigilant in shoring up our cyber defenses. The true stories of cyber espionage, hacking, and attacks recounted in his book are issues that we should all keep in mind as we navigate our own online lives, both personally and professionally. After all, “What has enriched our economy and quality of life for the past several decades,” Carlin opines, “may start to hurt us more than help us — until we confront its cybersecurity challenges.”
NIH is not immune to this issue. On any given day, NIH’s automated email threat detection technology automatically blocks more than 23 million threatening emails that may be phishing attempts or could include malware. Cybersecurity is a growing concern, one that impacts all of our functions. We all have the ability to protect these systems that we rely on every day for our work.
As many of you use NIH’s electronic Research Administration (eRA) and other NIH systems often, maybe even daily), it’s worth taking a step back to reflect on what these systems do. Why is cyber safety so important? Well, in FY2019, eRA and NIH systems:
- Published 1,757 Funding Opportunity Announcements (FOA’s)
- Processed 166,000 applications and awards
- Processed $35.5 billion in award obligations
- Had 870,000 registered users, with 243,000 of those active
- Handled 23.3 million logins
- Enabled the work of 63,100 reviewers who participated in 3,576 review meetings
- Added 7.12 million documents into government data bases
And the demands are growing. Since fiscal year 2008, we have observed steady growth in individual institutional (blue line) and user (red line) accounts by 11 percent and 10 percent annually, respectively (Figure 1).
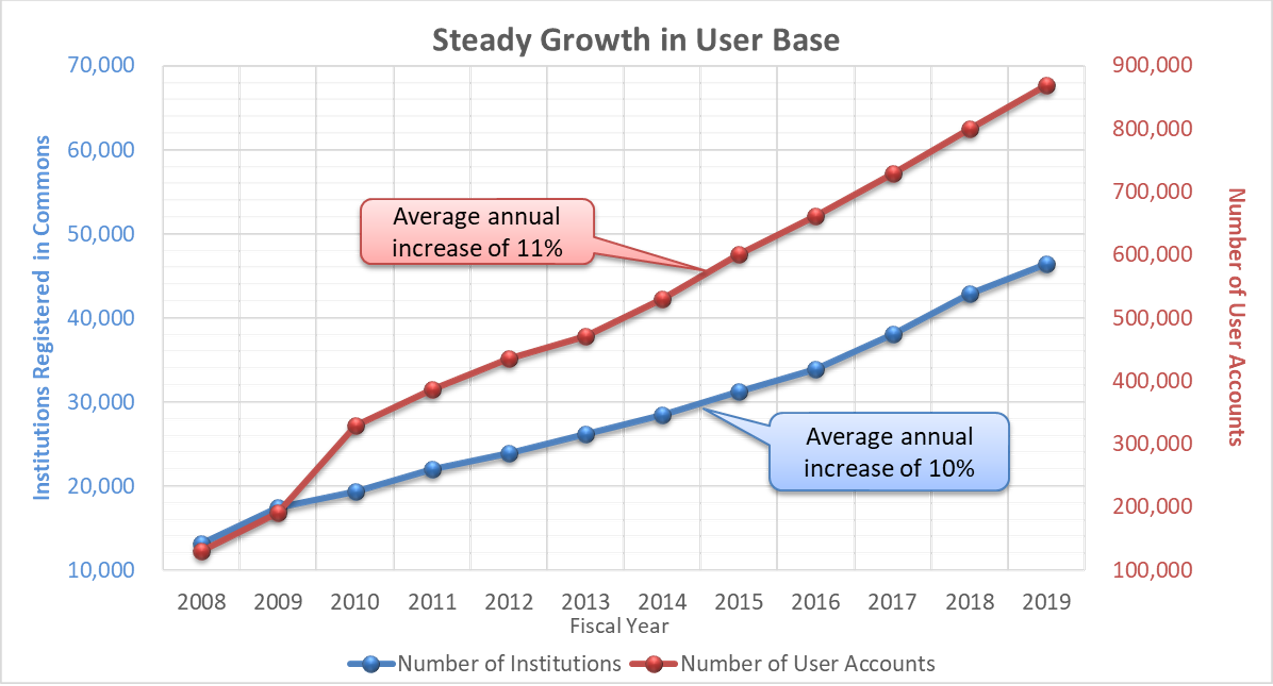
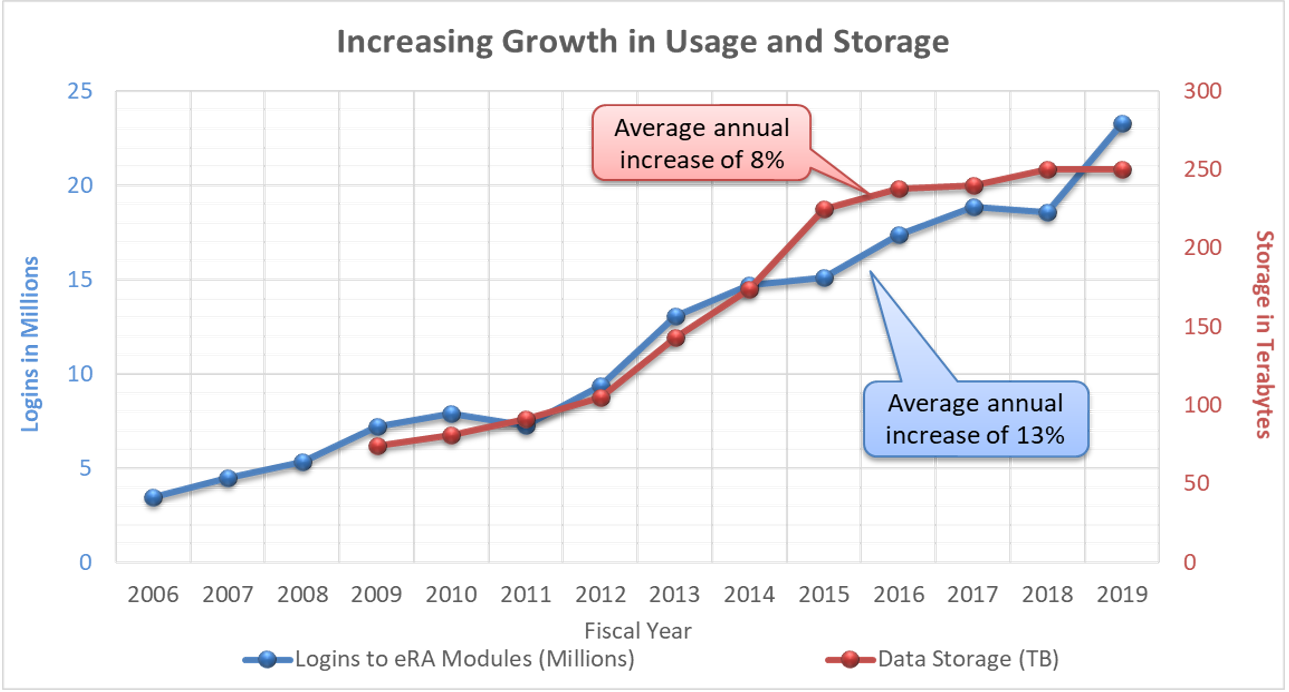
Figure 2 shows logins to eRA modules (blue line) rise about 13 percent annually. Data storage needs (red line) also increases, at a clip of 8 percent annually.
In other words – the stakes are high.
Over the next few months, we will post a series of essays on cyber safety and why it matters to all of us. We all depend on the safety and security of our systems in order to do our work – including interacting with NIH on billions of dollars of federally funded projects. To begin educating yourself about cyber safety, I invite you to take a look at this Department of Homeland Security site for some good advice. We should regularly consider these tips especially now during our current situation. For instance, cybercriminals are sending malicious phishing emails that appear to be from trusted federal agencies such as the Department of Health and Human Services and the Centers for Disease Control and Prevention, to steal sensitive data. Other phishing emails have contained a link to a malicious website that was designed to look like a live map of COVID-19 cases from Johns Hopkins University. We all have to remain vigilant and be ready to report if we see anything suspicious, and continuing to keep our work, data, and professional and personal lives safer and more productive.



This was a good if not great article on the facts of security. I work at a University and as far as I can see hardly any University has any security. Faculty can rarely be reined in. They do not realize that when they do some of their web crawling they bring home worms.
Now that some are instituting two factor authentication it will get better, Also realize many smaller Universities cant afford anything resembling a full time security staff.
I would appreciate any comments.
Cyber security is really important. It is important to educate workers on this, because many don’t think about it. This article is very interesting, thanks
Individual Hackers is the most problematic type of hackers as there are as many reasons why someone would steal any information as there are individual hackers. These persons usually use cyberstalking over social media and other methods and they usually fixate on specific targets.